
Servers are beating the hearts of countless businesses, housing critical data, running applications, and enabling seamless communication. Securing your server is no longer optional, as cyber threats are evolving quickly.
A compromised server can lead to data breaches, service disruptions, and loss of trust from clients and stakeholders. To help you safeguard your digital assets, here’s a creative, actionable guide packed with tips and best practices for strengthening your server security:
1. Implement A Strong Password Strategy: Say Goodbye To “12345”!
A weak password is leaving your server’s door unlocked. Hackers thrive on poorly chosen and predictable credentials. A common mistake is using simple passwords or keeping the default ones set by your 4u server software.
As per the report of Microsoft “ A strong password is at least 12-14 characters long, combines uppercase, lowercase, numbers, symbols, avoids dictionary words or names, and differs from previous passwords.”
 Source: PassCamp
Source: PassCamp
How to build strong passwords
- Go with complex combinations with at least 12 characters, including uppercase letters, lowercase letters, numbers, and special characters.
- Avoid using easily guessable information like names, birth dates, or dictionary words.
- Encourage using passphrases- a series of unrelated words strung together.
- Use password managers to generate and store strong passwords securely
- Enforce periodic password changes to reduce the risk of compromised credentials.
Strengthening your password strategy makes it exponentially harder for cybercriminals to gain unauthorized access.
2. Keep Your Software Up-To-Date: Don’t Ignore Those Annoying Prompts
If you’re in the habit of clicking “Remind me later” when prompted for updates, it’s time to rethink the approach you’re pushing. Outdated software is fertile ground for hackers who often exploit known vulnerabilities.
Why updates matter:
- Delaying updates exposes your server to attacks that target outdated versions.
- Many high-profile breaches have occurred simply because systems weren’t patched on time.
How to stay secure:
- Schedule automatic updates for your server software and operating systems.
- Maintain an inventory of all software and regularly check for available prices.
- Test updates in a staging environment before deploying them to production to ensure compatibility.
Note: Staying current with updates is a simple yet powerful way to close the doors hackers want to sneak through.
3. Implement Firewalls And Intrusion Detection Systems (IDS): Build A Digital Fort
Firewalls are your server’s first line of defense, filtering incoming and outgoing traffic to prevent unauthorized access. Coupled with Intrusion Detection Systems (IDS), they become a formidable security duo.
How to set up an effective firewall:
- Configure rules to block all non-essential traffic.
- Enable logging to track incoming and outgoing connections.
- Use both hardware and software firewalls for layered protection.
Why IDS matters:
- It monitors server traffic and flags suspicious activity, such as repeated login attempts or abnormal data transfers.
- Alerts enable you to respond quickly before significant damage occurs.
Together, firewalls and IDS form an essential shield against external threats.
4. Enable Secure Shell (SSH) And Disable Unnecessary Services: Keep It Lean And Safe
Plain-text communication protocols are a hacker’s dream. SSH encrypts data exchanges between your server and connected clients, making it a secure alternative to vulnerable protocols like Telnet.
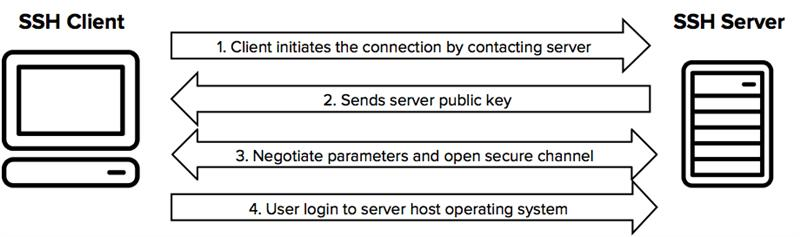
Source: SSH
Best practices for secure server access:
- Always use SSH for remote server management.
- Restrict SSH access to specific IP addresses to limit exposure.
- Use SSH keys instead of passwords for even stronger authentication.
Also, turn off any services and protocols not essential to your server’s operation. Unnecessary services provide potential entry points for attackers.
5. Monitor Logs Like A Hawk: Your Security Crystal Ball
Server logs are invaluable for understanding both normal and abnormal activities. They provide detailed records of login attempts, file changes, and network traffic.
Why log monitoring matters:
- It helps identify patterns that may indicate a security breach.
- Detects unauthorized access attempts and resource usage anomalies.
- Provides critical evidence for forensic analysis after a security incident.
How to monitor effectively:
- Automate log analysis with tools that flag unusual activities in real time.
- Set up alerts for critical events such as multiple failed login attempts.
- Regularly review logs to identify long-term trends.
By watching logs, you gain early warning signals that help prevent major incidents.
6. Limit User Access: Everyone Doesn’t Need The Keys
The more people with access to your server, the greater the risk. Not everyone needs administrative privileges, and most don’t.
How to manage user access:
- Follow the Principle of Least Privilege (POLP), giving users only the access they need to perform their tasks.
- Use role-based access controls (RBAC) to manage permissions effectively.
- Conduct periodic reviews of user accounts and promptly revoke access for former employees or unused accounts.
Limiting access reduces your attack surface and helps maintain tighter security controls.
7. Data Backups Are Non-Negotiable: Prepare For The Worst
Even with the best security measures, breaches and failures can happen. Regular backups ensure that you can quickly recover from data loss.
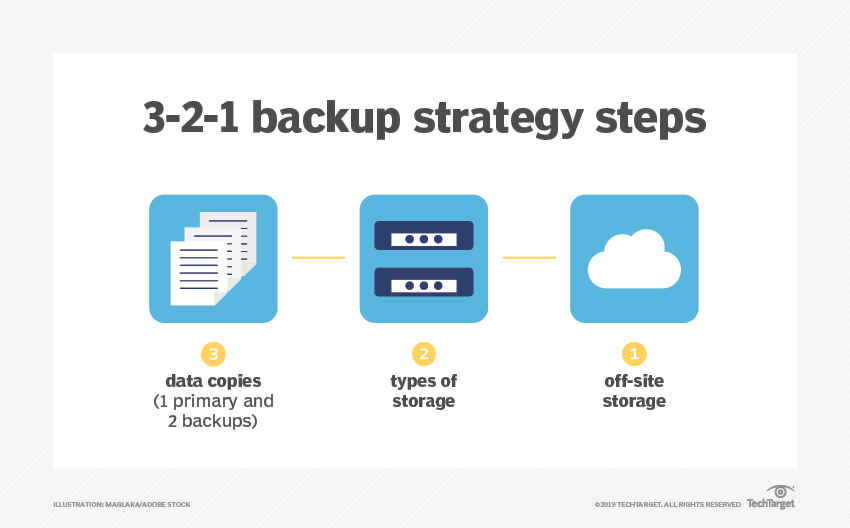 Source: TechTarget
Source: TechTarget
Backup best practices:
- Schedule automatic backups to avoid human error.
- Store backups in multiple locations, including secure offsite or cloud environments.
- Encrypt backup data to protect it from unauthorized access.
- Test restoration procedures to ensure data can be recovered seamlessly.
When disaster strikes, having a reliable backup strategy can be the difference between quick recovery and complete catastrophe.
Final Thoughts: Build A Fortress, Not Just A Server
Server security is a continuous journey, not a one-time task. Following these best practices and remaining vigilant can build a digital fortress that protects your business, data, and reputation. Remember, the key to successful security lies in proactive defense and adaptation to new challenges. Start strengthening your server security today and sleep easier knowing your digital assets are safe.






