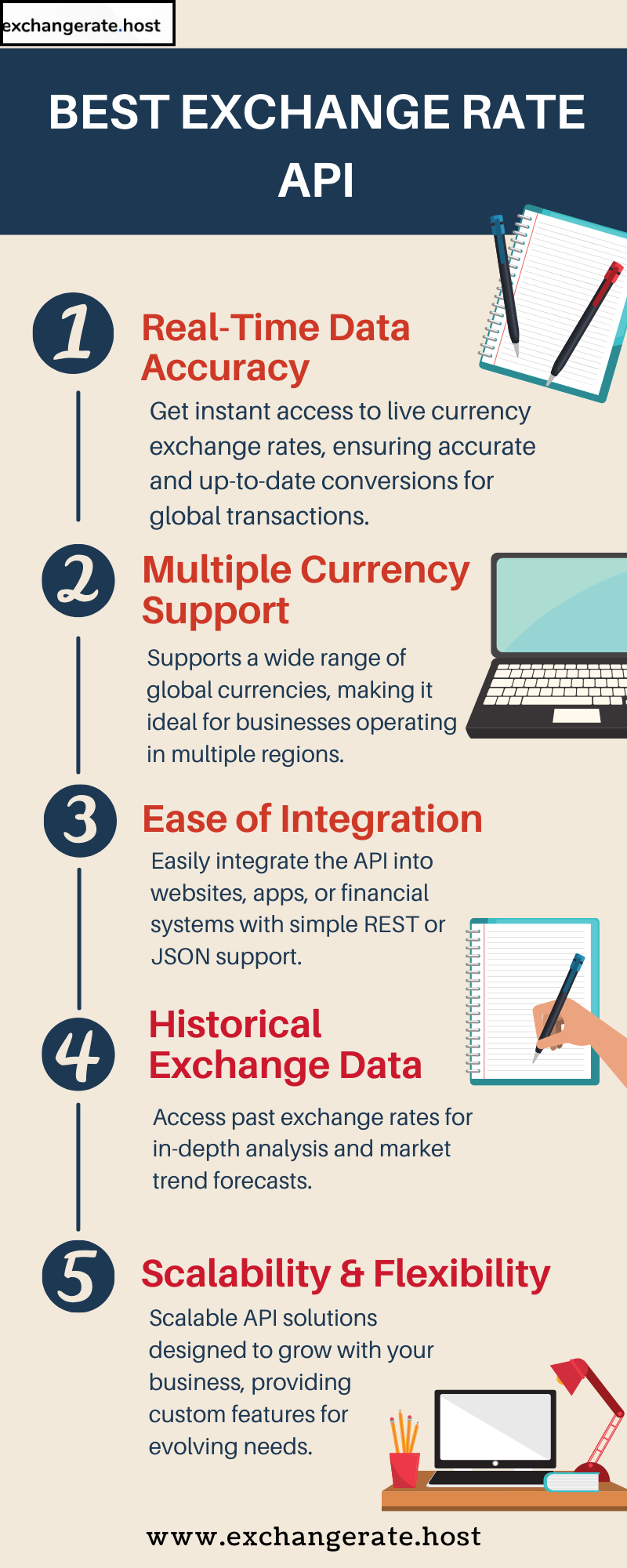
APIs have revolutionized the way developers access and use financial data, particularly in the realm of foreign exchange rates. However, with the sensitive nature of financial information, it is critical to secure this data properly to avoid potential breaches, cyber-attacks, or misuse. In this article, we’ll explore best practices for ensuring data security when using foreign exchange rate APIs, targeting developers and IT professionals working with financial applications.
The Importance of Securing Financial Data
Foreign exchange rate APIs provide real-time access to currency conversion rates, a vital service for businesses involved in global trade, e-commerce platforms, financial institutions, and travel-related services. However, since these APIs often deal with sensitive financial data, such as currency conversions linked to transactions or customer financial details, protecting this information from unauthorized access is paramount.
APIs are highly exposed to security vulnerabilities due to the open nature of their communication protocols, especially if security measures are not robustly enforced. Compromised financial data can lead to monetary loss, reputation damage, or legal repercussions, making API security a critical component of any system handling foreign exchange rate data.
Best Practices for Securing Foreign Exchange Rate APIs
1. Use HTTPS for Secure Communication
Always ensure that your foreign exchange rate API interactions occur over HTTPS, not HTTP. HTTPS encrypts the data transmitted between the client (your application) and the API server, preventing third parties from eavesdropping on sensitive information such as API keys, currency conversion results, or financial transaction data. HTTPS ensures that even if an attacker intercepts the data, they cannot easily decipher it.
2. API Key Management and Authentication
API keys are often the first line of defense in securing API access. They act as unique identifiers that authenticate your requests to the foreign exchange rate API. To protect your API keys:
- Keep them secret: Never expose your API keys in client-side code or public repositories.
- Use environment variables: Store your API keys in environment variables to keep them hidden from unauthorized users.
- Rotate API keys regularly: Implement a key rotation policy to minimize risk in case your keys are compromised.
- Use OAuth: If the API provider supports OAuth, use it to add an extra layer of security for authentication, ensuring that only authorized clients can access the data.
3. Encrypt Sensitive Data
While HTTPS secures the transmission of data, it’s also important to encrypt sensitive financial data at rest. For instance, if your application stores foreign exchange rate data locally, ensure that the data is encrypted using strong encryption algorithms like AES-256.
4. Implement Rate Limiting and Quotas
Rate limiting is a practice where you set limits on the number of API requests a user or an application can make over a given time period. This not only prevents abuse but also mitigates potential security threats such as Denial of Service (DoS) attacks. Implementing API quotas ensures that even if an API key is compromised, the attacker cannot flood your system with unlimited requests.
5. Monitor API Usage
Monitoring your foreign exchange rate API usage is crucial for detecting unusual behavior or potential security threats. Keep track of how often the API is called, what kind of data is requested, and from where the requests originate. Use monitoring tools to set up alerts for unusual spikes in usage or abnormal access patterns, which can be signs of a security breach.
6. Validate Data and Sanitize Inputs
APIs can be vulnerable to attacks like SQL injection or code injection if inputs are not properly validated. Always validate and sanitize any input data that your application sends to the API. Implement strict parameter validation to prevent malicious inputs from compromising the system or fetching unauthorized financial data.
7. Use IP Whitelisting
IP whitelisting adds an extra layer of security by ensuring that only requests coming from authorized IP addresses can access the foreign exchange rate API. By limiting access to specific, trusted IP addresses, you reduce the risk of unauthorized or malicious actors gaining access to sensitive financial data.
8. Enable Two-Factor Authentication (2FA)
If possible, integrate two-factor authentication (2FA) with your API authentication processes. 2FA requires users to verify their identity through an additional method beyond just the API key, such as a one-time code sent to their email or phone. This significantly enhances security, especially when dealing with sensitive financial data related to foreign exchange rates.
9. Implement Logging and Auditing
Set up proper logging and auditing mechanisms to track API usage, access patterns, and security incidents. Logs can help identify unauthorized access or other anomalies in real time. Additionally, maintaining an audit trail ensures that you can investigate incidents effectively and take corrective measures to prevent future breaches.
10. Regular Security Audits and Penetration Testing
Finally, conduct regular security audits and penetration testing on your foreign exchange rate API infrastructure. By simulating potential attacks, you can identify vulnerabilities before malicious actors exploit them. Regularly reviewing your security practices ensures that your system remains compliant with the latest security standards and that your financial data is protected against new threats.
Conclusion
When integrating foreign exchange rate APIs into your financial applications, prioritizing data security is crucial. As financial data is particularly sensitive, following best practices such as using HTTPS, encrypting data, managing API keys properly, and monitoring API usage can greatly reduce the risk of security breaches. Developers and IT professionals must stay proactive in implementing these measures to protect sensitive financial information from unauthorized access, ensuring a secure and reliable experience for end users.




